Customize Web Application Firewall rules using the Azure portal
The Azure Application Gateway Web Application Firewall (WAF) provides protection for web applications. These protections are provided by the Open Web Application Security Project (OWASP) Core Rule Set (CRS). Some rules can cause false positives and block real traffic. For this reason, Application Gateway provides the capability to customize rule groups and rules. For more information on the specific rule groups and rules, see List of Web Application Firewall CRS rule groups and rules.
Note
If your application gateway is not using the WAF tier, the option to upgrade the application gateway to the WAF tier appears in the right pane.
View rule groups and rules
To view rule groups and rules
Browse to the application gateway, and then select Web application firewall.
Select your WAF Policy.
Select Managed Rules.
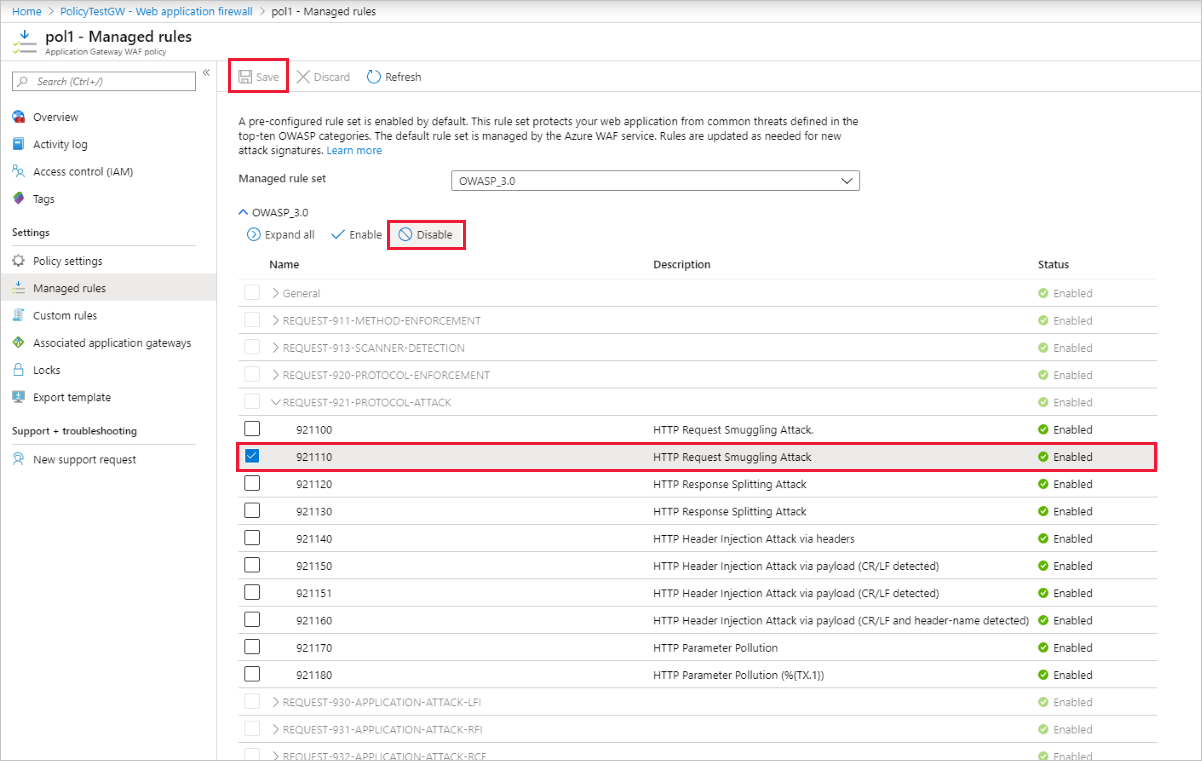
This view shows a table on the page of all the rule groups provided with the chosen rule set. All of the rule's check boxes are selected.
Disable rule groups and rules
Important
Use caution when disabling any rule groups or rules. This may expose you to increased security risks. The anomaly score is not incremented and no logging happens for disabled rules.
To disable rule groups or specific rules
- Search for the rules or rule groups that you want to disable.
- Select the check boxes for the rules that you want to disable.
- Select the action at the top of the page (enable/disable) for the selected rules.
- Select Save.
Mandatory rules
The following list contains conditions that cause the WAF to block the request while in Prevention Mode. In Detection Mode, they're logged as exceptions.
These can't be configured or disabled:
- Failure to parse the request body results in the request being blocked, unless body inspection is turned off (XML, JSON, form data)
- Request body (with no files) data length is larger than the configured limit
- Request body (including files) is larger than the limit
- An internal error happened in the WAF engine
CRS 3.x specific:
- Inbound anomaly score exceeded threshold
Next steps
After you configure your disabled rules, you can learn how to view your WAF logs. For more information, see Application Gateway diagnostics.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for