Overview of Container security in Microsoft Defender for Containers
Microsoft Defender for Containers is a cloud-native solution to improve, monitor, and maintain the security of your containerized assets (Kubernetes clusters, Kubernetes nodes, Kubernetes workloads, container registries, container images and more), and their applications, across multicloud and on-premises environments.
Defender for Containers assists you with four core domains of container security:
Security posture management - performs continuous monitoring of cloud APIs, Kubernetes APIs, and Kubernetes workloads to discover cloud resources, provide comprehensive inventory capabilities, detect misconfigurations and provide guidelines to mitigate them, provide contextual risk assessment, and empowers users to perform enhanced risk hunting capabilities through the Defender for Cloud security explorer.
Vulnerability assessment - provides agentless vulnerability assessment for Azure, AWS, and GCP with remediation guidelines, zero configuration, daily rescans, coverage for OS and language packages, and exploitability insights.
Run-time threat protection - a rich threat detection suite for Kubernetes clusters, nodes, and workloads, powered by Microsoft leading threat intelligence, provides mapping to MITRE ATT&CK framework for easy understanding of risk and relevant context, automated response, and SIEM/XDR integration.
Deployment & monitoring- Monitors your Kubernetes clusters for missing sensors and provides frictionless at-scale deployment for sensor-based capabilities, support for standard Kubernetes monitoring tools, and management of unmonitored resources.
You can learn more by watching this video from the Defender for Cloud in the Field video series: Microsoft Defender for Containers.
Microsoft Defender for Containers plan availability
| Aspect | Details |
|---|---|
| Release state: | General availability (GA) Certain features are in preview. For a full list, see the Containers support matrix in Defender for Cloud |
| Feature availability | Refer to the Containers support matrix in Defender for Cloud for additional information on feature release state and availability. |
| Pricing: | Microsoft Defender for Containers is billed as shown on the pricing page |
| Required roles and permissions: | • To deploy the required components, see the permissions for each of the components • Security admin can dismiss alerts • Security reader can view vulnerability assessment findings See also Roles for remediation and Azure Container Registry roles and permissions |
| Clouds: | View the Containers support matrix in Defender for Cloud to see cloud availability. |
Security posture management
Agentless capabilities
Agentless discovery for Kubernetes - provides zero footprint, API-based discovery of your Kubernetes clusters, their configurations and deployments.
Agentless vulnerability assessment - provides vulnerability assessment for all container images, including recommendations for registry and runtime, quick scans of new images, daily refresh of results, exploitability insights, and more. Vulnerability information is added to the security graph for contextual risk assessment and calculation of attack paths, and hunting capabilities.
Comprehensive inventory capabilities - enables you to explore resources, pods, services, repositories, images and configurations through security explorer to easily monitor and manage your assets.
Enhanced risk-hunting - enables security admins to actively hunt for posture issues in their containerized assets through queries (built-in and custom) and security insights in the security explorer
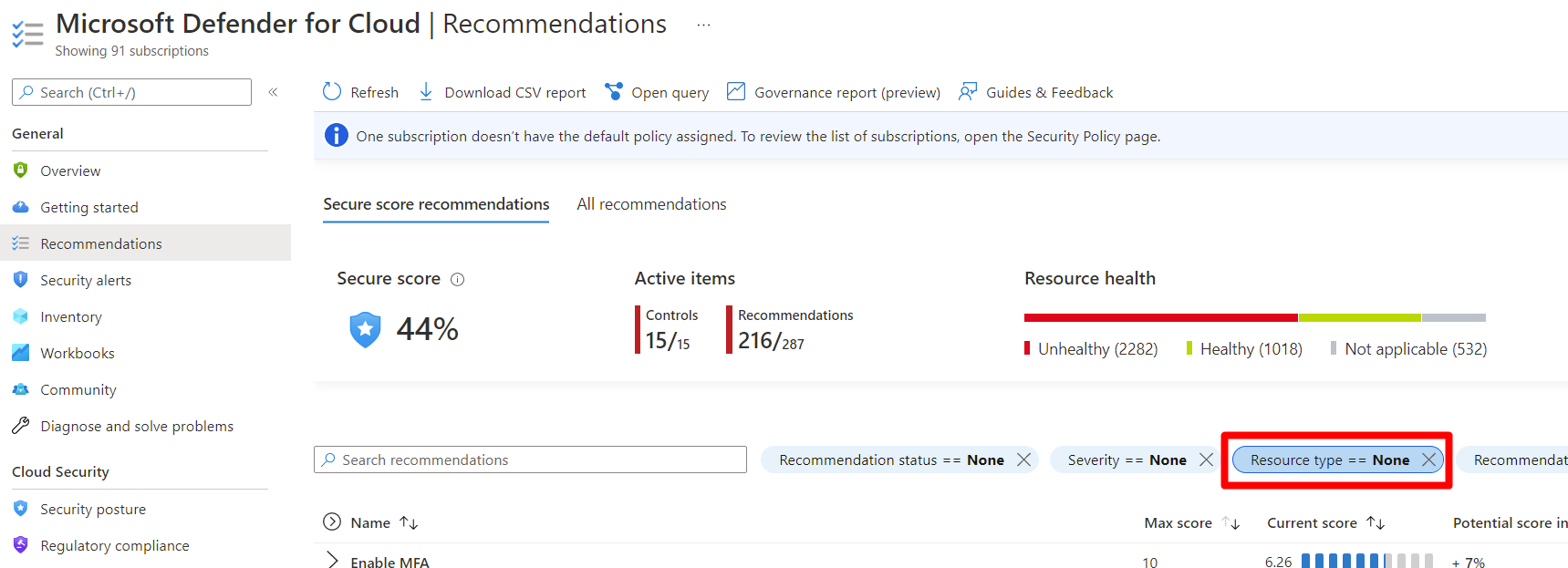
Control plane hardening - continuously assesses the configurations of your clusters and compares them with the initiatives applied to your subscriptions. When it finds misconfigurations, Defender for Cloud generates security recommendations that are available on Defender for Cloud's Recommendations page. The recommendations let you investigate and remediate issues.
You can use the resource filter to review the outstanding recommendations for your container-related resources, whether in asset inventory or the recommendations page:
For details included with this capability, check out the containers section of the recommendations reference table, and look for recommendations with type "Control plane"
Sensor-based capabilities
Kubernetes data plane hardening - To protect the workloads of your Kubernetes containers with best practice recommendations, you can install the Azure Policy for Kubernetes. Learn more about monitoring components for Defender for Cloud.
With the add-on on your Kubernetes cluster, every request to the Kubernetes API server is monitored against the predefined set of best practices before being persisted to the cluster. You can then configure it to enforce the best practices and mandate them for future workloads.
For example, you can mandate that privileged containers shouldn't be created, and any future requests to do so are blocked.
You can learn more about Kubernetes data plane hardening.
Vulnerability assessment
Defender for Containers scans the container images in Azure Container Registry (ACR), Amazon AWS Elastic Container Registry (ECR), Google Artifact Registry (GAR), and Google Container Registry (GCR) to provide agentless vulnerability assessment for your container images, including registry and runtime recommendations, remediation guidance, quick scans of new images, real-world exploit insights, exploitability insights, and more.
Vulnerability information powered by Microsoft Defender Vulnerability Management is added to the cloud security graph for contextual risk, calculation of attack paths, and hunting capabilities.
Learn more about:
- Vulnerability assessments for Azure with Microsoft Defender Vulnerability Management
- Vulnerability assessments for AWS with Microsoft Defender Vulnerability Management
- Vulnerability assessments for GCP with Microsoft Defender Vulnerability Management
Run-time protection for Kubernetes nodes and clusters
Defender for Containers provides real-time threat protection for supported containerized environments and generates alerts for suspicious activities. You can use this information to quickly remediate security issues and improve the security of your containers.
Threat protection is provided for Kubernetes at cluster level, node level, and workload level and includes both sensor based coverage that requires the Defender sensor and agentless coverage that is based on analysis of the Kubernetes audit logs. Security alerts are only triggered for actions and deployments that occur after you enabled Defender for Containers on your subscription.
Examples of security events that Microsoft Defenders for Containers monitors include:
- Exposed Kubernetes dashboards
- Creation of high privileged roles
- Creation of sensitive mounts
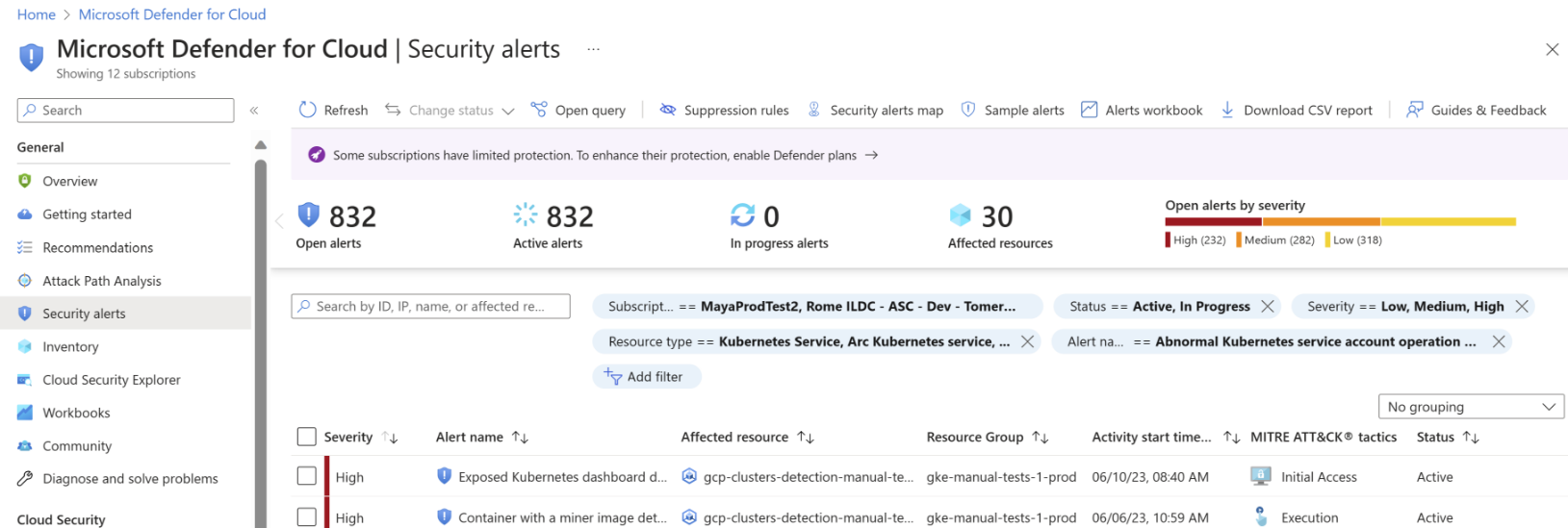
You can view security alerts by selecting the Security alerts tile at the top of the Defender for Cloud's overview page, or the link from the sidebar.
The security alerts page opens:
Security alerts for runtime workload in the clusters can be recognized by the K8S.NODE_ prefix of the alert type. For a full list of the cluster level alerts, see the reference table of alerts.
Defender for Containers also includes host-level threat detection with over 60 Kubernetes-aware analytics, AI, and anomaly detections based on your runtime workload.
Defender for Cloud monitors the attack surface of multicloud Kubernetes deployments based on the MITRE ATT&CK® matrix for Containers, a framework developed by the Center for Threat-Informed Defense in close partnership with Microsoft.
Learn more
Learn more about Defender for Containers in the following blogs:
Next steps
In this overview, you learned about the core elements of container security in Microsoft Defender for Cloud. To enable the plan, see:
- Enable Defender for Containers
- Check out common questions about Defender for Containers.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for