VPN Gateway topology and design
There are many different configuration options available for VPN Gateway connections. Use the diagrams and descriptions in the following sections to help you select the connection topology that meets your requirements. The diagrams show the main baseline topologies, but it's possible to build more complex configurations using the diagrams as guidelines.
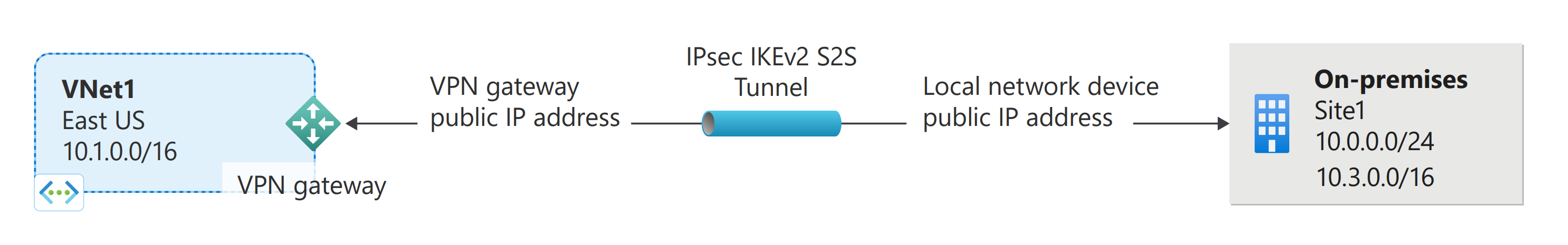
Site-to-site VPN
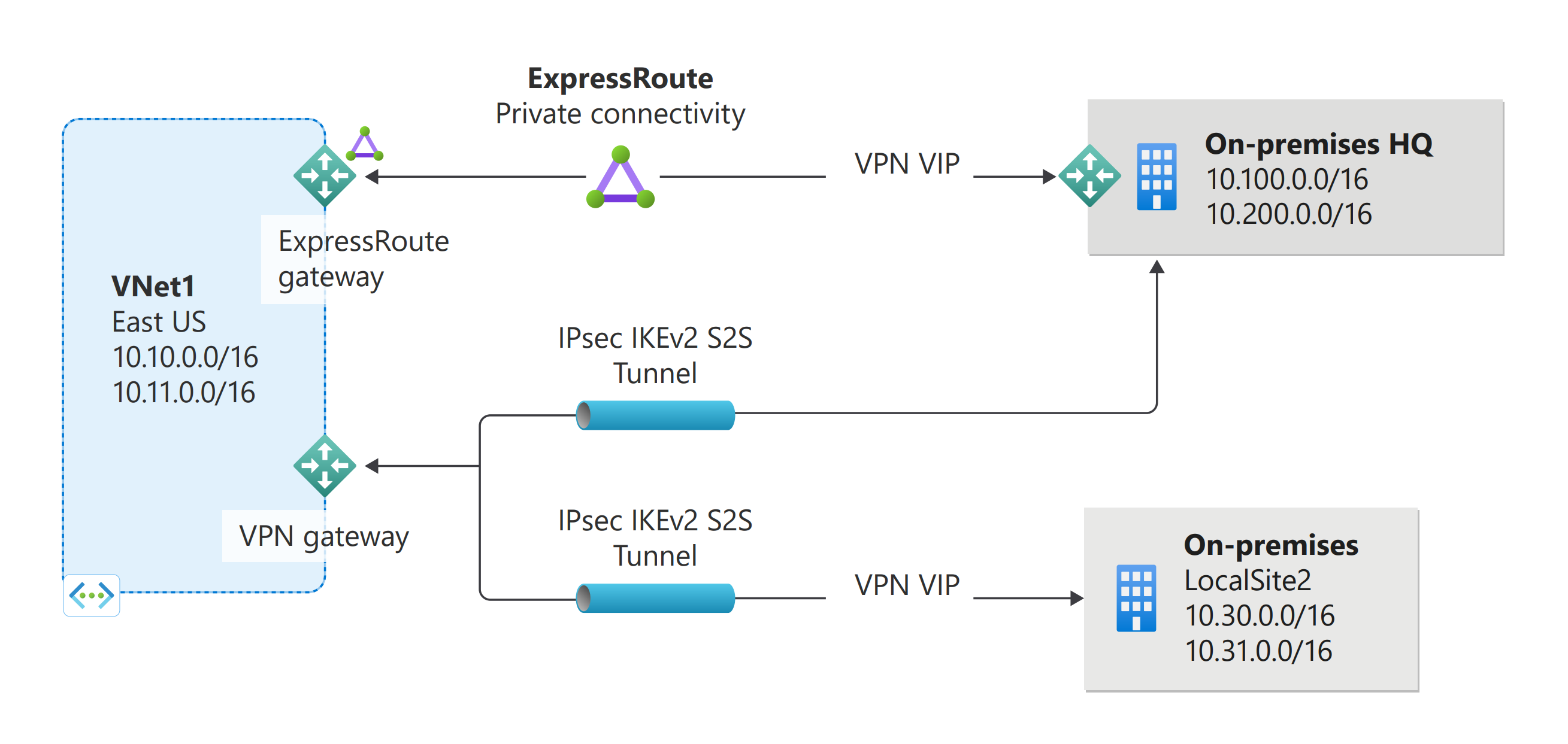
A site-to-site (S2S) VPN gateway connection is a connection over IPsec/IKE (IKEv1 or IKEv2) VPN tunnel. Site-to-site connections can be used for cross-premises and hybrid configurations. A site-to-site connection requires a VPN device located on-premises that has a public IP address assigned to it. For information about selecting a VPN device, see the VPN Gateway FAQ - VPN devices.
VPN Gateway can be configured in active-standby mode using one public IP or in active-active mode using two public IPs. In active-standby mode, one IPsec tunnel is active and the other tunnel is in standby. In this setup, traffic flows through the active tunnel, and if some issue happens with this tunnel, the traffic switches over to the standby tunnel. Setting up VPN Gateway in active-active mode is recommended in which both the IPsec tunnels are simultaneously active, with data flowing through both tunnels at the same time. Another advantage of active-active mode is that customers experience higher throughputs.
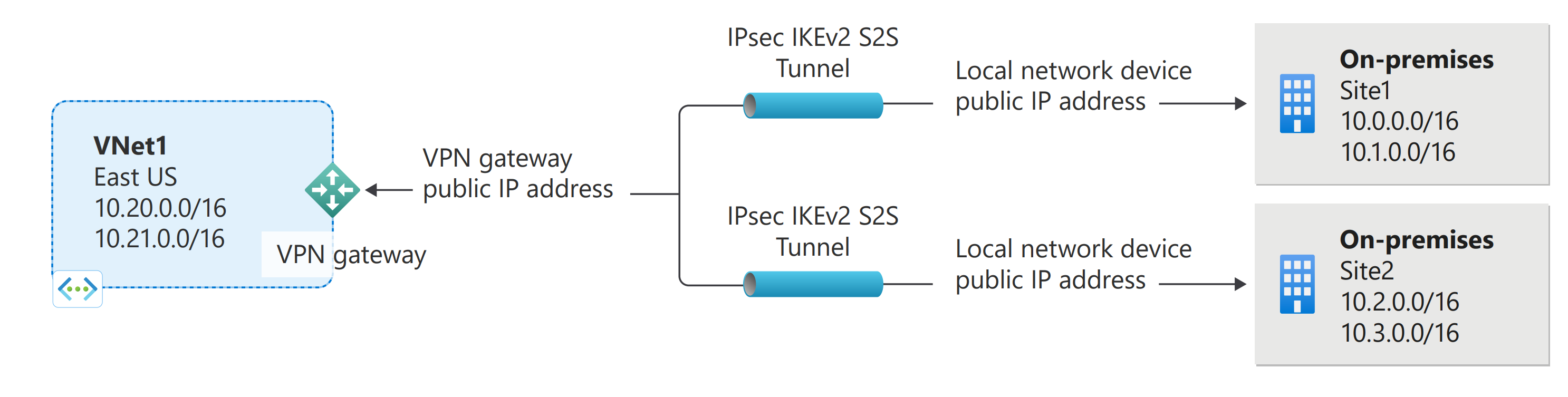
You can create more than one VPN connection from your virtual network gateway, typically connecting to multiple on-premises sites. When working with multiple connections, you must use a RouteBased VPN type (known as a dynamic gateway when working with classic VNets). Because each virtual network can only have one VPN gateway, all connections through the gateway share the available bandwidth. This type of connection is sometimes referred to as a "multi-site" connection.
Deployment models and methods for S2S
| Deployment model/method | Azure portal | PowerShell | Azure CLI |
|---|---|---|---|
| Resource Manager | Tutorial | Tutorial | Tutorial |
| Classic (legacy deployment model) | Tutorial** | Tutorial | Not Supported |
(**) denotes that this method contains steps that require PowerShell.
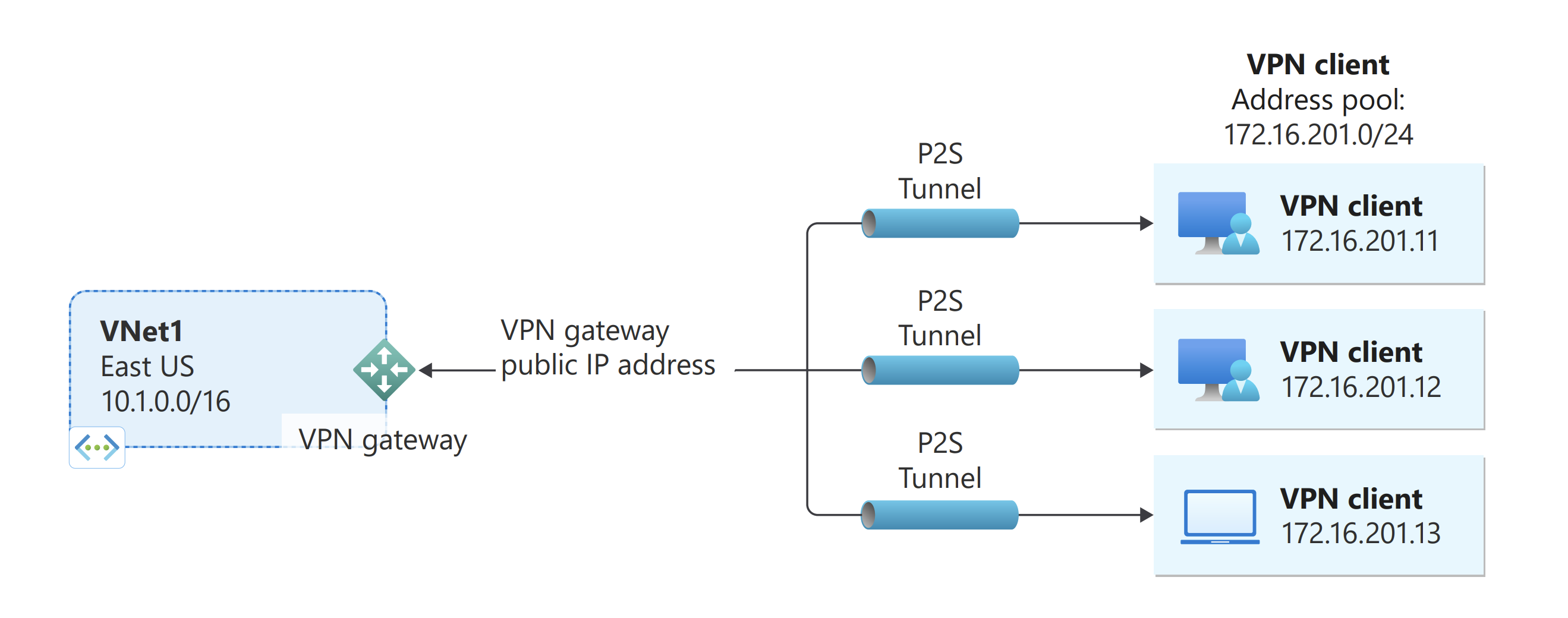
Point-to-site VPN
A point-to-site (P2S) VPN gateway connection lets you create a secure connection to your virtual network from an individual client computer. A point-to-site connection is established by starting it from the client computer. This solution is useful for telecommuters who want to connect to Azure virtual networks from a remote location, such as from home or a conference. Point-to-site VPN is also a useful solution to use instead of site-to-site VPN when you have only a few clients that need to connect to a virtual network.
Unlike site-to-site connections, point-to-site connections don't require an on-premises public-facing IP address or a VPN device. Point-to-site connections can be used with site-to-site connections through the same VPN gateway, as long as all the configuration requirements for both connections are compatible. For more information about point-to-site connections, see About point-to-site VPN.
Deployment models and methods for P2S
| Authentication method | Article |
|---|---|
| Certificate | Tutorial How-to |
| Microsoft Entra ID | How-to |
| RADIUS | How-to |
P2S VPN client configuration
| Authentication | Tunnel type | Client OS | VPN client |
|---|---|---|---|
| Certificate | |||
| IKEv2, SSTP | Windows | Native VPN client | |
| IKEv2 | macOS | Native VPN client | |
| IKEv2 | Linux | strongSwan | |
| OpenVPN | Windows | Azure VPN client OpenVPN client |
|
| OpenVPN | macOS | OpenVPN client | |
| OpenVPN | iOS | OpenVPN client | |
| OpenVPN | Linux | Azure VPN Client OpenVPN client |
|
| Microsoft Entra ID | |||
| OpenVPN | Windows | Azure VPN client | |
| OpenVPN | macOS | Azure VPN Client | |
| OpenVPN | Linux | Azure VPN Client |
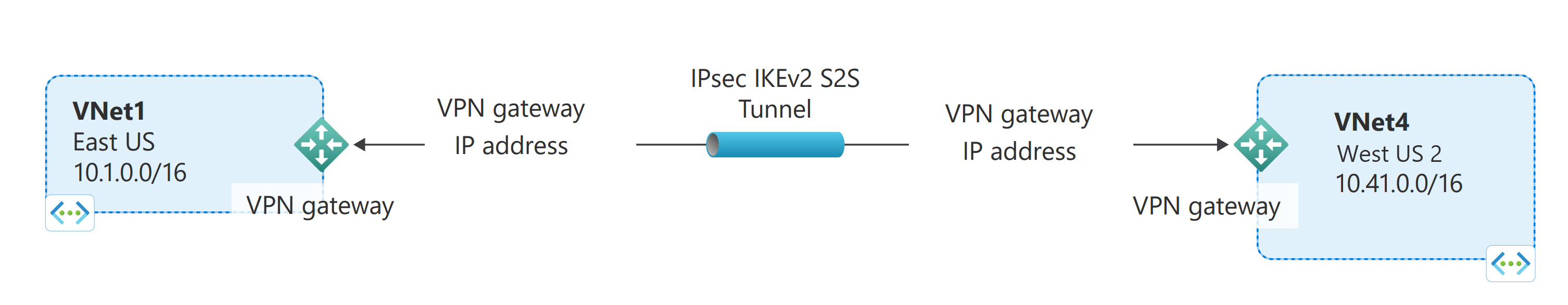
VNet-to-VNet connections (IPsec/IKE VPN tunnel)
Connecting a virtual network to another virtual network (VNet-to-VNet) is similar to connecting a virtual network to an on-premises site location. Both connectivity types use a VPN gateway to provide a secure tunnel using IPsec/IKE. You can even combine VNet-to-VNet communication with multi-site connection configurations. This lets you establish network topologies that combine cross-premises connectivity with inter-virtual network connectivity.
The virtual networks you connect can be:
- in the same or different regions
- in the same or different subscriptions
- in the same or different deployment models
Deployment models and methods for VNet-to-VNet
| Deployment model/method | Azure portal | PowerShell | Azure CLI |
|---|---|---|---|
| Resource Manager | Tutorial+ | Tutorial | Tutorial |
| Classic (legacy deployment model) | Tutorial* | Supported | Not Supported |
| Connections between Resource Manager and Classic (legacy) deployment models | Tutorial* | Tutorial | Not Supported |
(+) denotes this deployment method is available only for VNets in the same subscription.
(*) denotes that this deployment method also requires PowerShell.
In some cases, you might want to use virtual network peering instead of VNet-to-VNet to connect your virtual networks. Virtual network peering doesn't use a virtual network gateway. For more information, see Virtual network peering.
Site-to-site and ExpressRoute coexisting connections
ExpressRoute is a direct, private connection from your WAN (not over the public Internet) to Microsoft Services, including Azure. Site-to-site VPN traffic travels encrypted over the public Internet. Being able to configure site-to-site VPN and ExpressRoute connections for the same virtual network has several advantages.
You can configure a site-to-site VPN as a secure failover path for ExpressRoute, or use site-to-site VPNs to connect to sites that aren't part of your network, but that are connected through ExpressRoute. Notice that this configuration requires two virtual network gateways for the same virtual network, one using the gateway type Vpn, and the other using the gateway type ExpressRoute.
Deployment models and methods for S2S and ExpressRoute coexisting connections
| Deployment model/method | Azure portal | PowerShell |
|---|---|---|
| Resource Manager | Supported | Tutorial |
| Classic (legacy deployment model) | Not Supported | Tutorial |
Highly available connections
For planning and design for highly available connections, see Highly available connections.
Next steps
View the VPN Gateway FAQ for additional information.
Learn more about VPN Gateway configuration settings.
For VPN Gateway BGP considerations, see About BGP.
View the Subscription and service limits.
Learn about some of the other key networking capabilities of Azure.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for