How to enable LDAP authentication in Azure Managed Instance for Apache Cassandra
Azure Managed Instance for Apache Cassandra provides automated deployment and scaling operations for managed open-source Apache Cassandra data centers. This article discusses how to enable LDAP authentication to your clusters and data centers.
Important
LDAP authentication is in public preview. This feature is provided without a service level agreement, and it's not recommended for production workloads. For more information, see Supplemental Terms of Use for Microsoft Azure Previews.
Prerequisites
- If you don't have an Azure subscription, create a free account before you begin.
- An Azure Managed Instance for Apache Cassandra cluster. Review how to create an Azure Managed Instance for Apache Cassandra cluster from the Azure portal.
Deploy an LDAP Server in Azure
In this section, we'll walk through creating a simple LDAP server on a Virtual Machine in Azure. If you already have an LDAP server running, you can skip this section and review how to enable LDAP authentication.
Deploy a Virtual Machine in Azure using Ubuntu Server 18.04 LTS. You can follow instructions here.
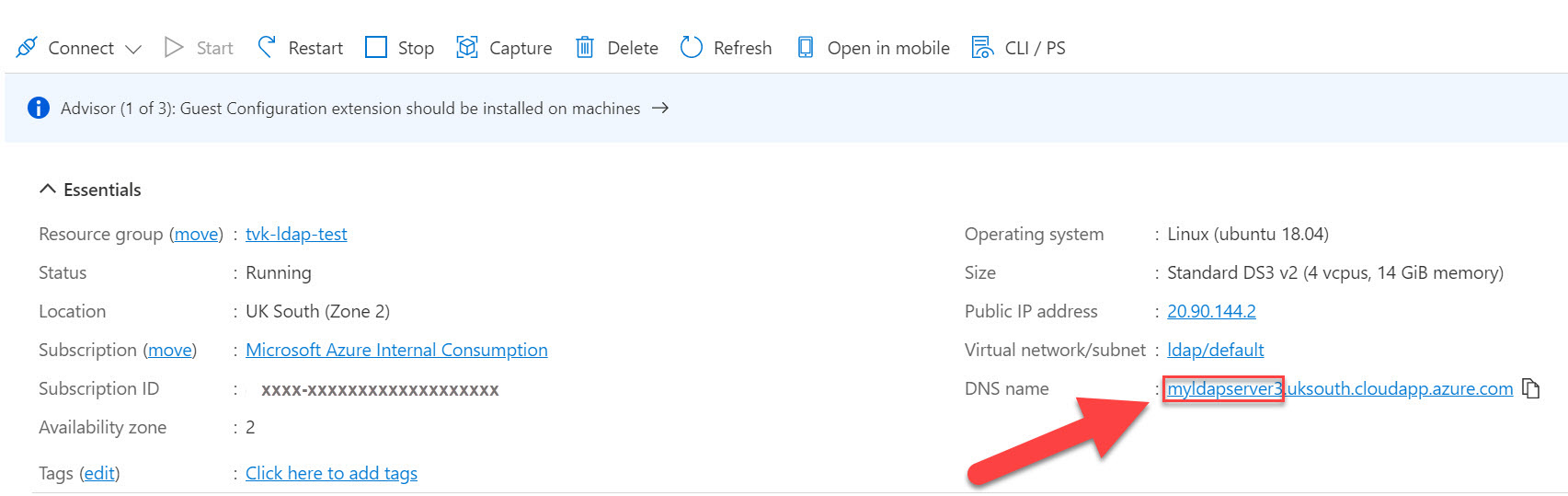
Give your server a DNS name:
Install Docker on the virtual machine. We recommend this tutorial.
In the home directory, copy and paste the following text and hit enter. This command will create a file containing a test LDAP user account.
mkdir ldap-user && cd ldap-user && cat >> user.ldif <<EOL dn: uid=admin,dc=example,dc=org uid: admin cn: admin sn: 3 objectClass: top objectClass: posixAccount objectClass: inetOrgPerson loginShell: /bin/bash homeDirectory: /home/admin uidNumber: 14583102 gidNumber: 14564100 userPassword: admin mail: admin@example.com gecos: admin EOLNavigate back up to home directory
cd ..Run the below command, replacing
<dnsname>with the dns name you created for your LDAP server earlier. This command will deploy an LDAP server with TLS enabled to a Docker container, and will also copy the user file you created earlier to the container.sudo docker run --hostname <dnsname>.uksouth.cloudapp.azure.com --name <dnsname> -v $(pwd)/ldap-user:/container/service/slapd/assets/test --detach osixia/openldap:1.5.0Now copy out the certificates folder from the container (replace
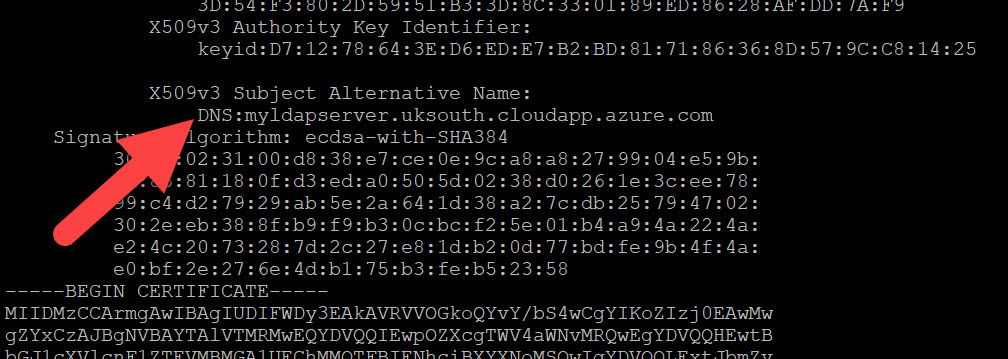
<dnsname>with the dns name you created for your LDAP server):sudo docker cp <dnsname>:/container/service/slapd/assets/certs certsVerify that dns name is correct:
openssl x509 -in certs/ldap.crt -textCopy the
ldap.crtfile to clouddrive in Azure CLI for use later.Add the user to the ldap (replace
<dnsname>with the dns name you created for your LDAP server):sudo docker container exec <dnsname> ldapadd -H ldap://<dnsname>.uksouth.cloudapp.azure.com -D "cn=admin,dc=example,dc=org" -w admin -f /container/service/slapd/assets/test/user.ldif
Enable LDAP authentication
Important
If you skipped the above section because you already have an existing LDAP server, please ensure that it has server SSL certificates enabled. The subject alternative name (dns name) specified for the certificate must also match the domain of the server that LDAP is hosted on, or authentication will fail.
Currently, LDAP authentication is a public preview feature. Run the below command to add the required Azure CLI extension:
az extension add --upgrade --name cosmosdb-previewSet authentication method to "Ldap" on the cluster, replacing
<resource group>and<cluster name>with the appropriate values:az managed-cassandra cluster update -g <resource group> -c <cluster name> --authentication-method "Ldap"Now set properties at the data center level. Replace
<resource group>and<cluster name>with the appropriate values, and<dnsname>with the dns name you created for your LDAP server.Note
The below command is based on the LDAP setup in the earlier section. If you skipped that section because you already have an existing LDAP server, provide the corresponding values for that server instead. Ensure you have uploaded a certificate file like
ldap.crtto your clouddrive in Azure CLI.ldap_search_base_distinguished_name='dc=example,dc=org' ldap_server_certificates='/usr/csuser/clouddrive/ldap.crt' ldap_server_hostname='<dnsname>.uksouth.cloudapp.azure.com' ldap_service_user_distinguished_name='cn=admin,dc=example,dc=org' ldap_service_user_password='admin' az managed-cassandra datacenter update -g `<resource group>` -c `<cluster name>` -d datacenter-1 --ldap-search-base-dn $ldap_search_base_distinguished_name --ldap-server-certs $ldap_server_certificates --ldap-server-hostname $ldap_server_hostname --ldap-service-user-dn $ldap_service_user_distinguished_name --ldap-svc-user-pwd $ldap_service_user_passwordOnce this command has completed, you should be able to use CQLSH (see below) or any Apache Cassandra open-source client driver to connect to your managed instance data center with the user added in the above step:
export SSL_VALIDATE=false cqlsh --debug --ssl <data-node-ip> -u <user> -p <password>
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for