What is Microsoft Entra Domain Services?
Microsoft Entra Domain Services provides managed domain services such as domain join, group policy, lightweight directory access protocol (LDAP), and Kerberos/NTLM authentication. You use these domain services without the need to deploy, manage, and patch domain controllers (DCs) in the cloud.
A Domain Services managed domain lets you run legacy applications in the cloud that can't use modern authentication methods, or where you don't want directory lookups to always go back to an on-premises AD DS environment. You can lift and shift those legacy applications from your on-premises environment into a managed domain, without needing to manage the AD DS environment in the cloud.
Domain Services integrates with your existing Microsoft Entra tenant. This integration lets users sign in to services and applications connected to the managed domain using their existing credentials. You can also use existing groups and user accounts to secure access to resources. These features provide a smoother lift-and-shift of on-premises resources to Azure.
Take a look at our short video to learn more about Domain Services.
How does Domain Services work?
When you create a Domain Services managed domain, you define a unique namespace. This namespace is the domain name, such as aaddscontoso.com. Two Windows Server domain controllers (DCs) are then deployed into your selected Azure region. This deployment of DCs is known as a replica set.
You don't need to manage, configure, or update these DCs. The Azure platform handles the DCs as part of the managed domain, including backups and encryption at rest using Azure Disk Encryption.
A managed domain is configured to perform a one-way synchronization from Microsoft Entra ID to provide access to a central set of users, groups, and credentials. You can create resources directly in the managed domain, but they aren't synchronized back to Microsoft Entra ID. Applications, services, and VMs in Azure that connect to the managed domain can then use common AD DS features such as domain join, group policy, LDAP, and Kerberos/NTLM authentication.
In a hybrid environment with an on-premises AD DS environment, Microsoft Entra Connect synchronizes identity information with Microsoft Entra ID, which is then synchronized to the managed domain.
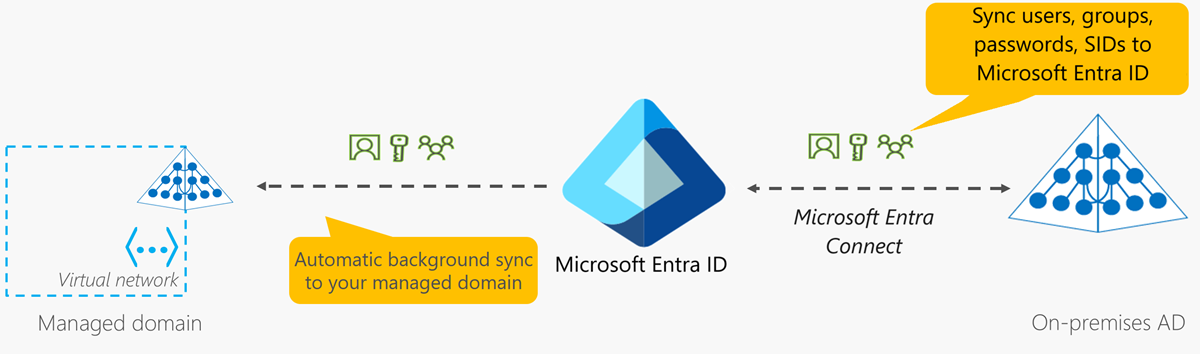
Domain Services replicates identity information from Microsoft Entra ID, so it works with Microsoft Entra tenants that are cloud-only, or synchronized with an on-premises AD DS environment. The same set of Domain Services features exists for both environments.
- If you have an existing on-premises AD DS environment, you can synchronize user account information to provide a consistent identity for users. To learn more, see How objects and credentials are synchronized in a managed domain.
- For cloud-only environments, you don't need a traditional on-premises AD DS environment to use the centralized identity services of Domain Services.
You can expand a managed domain to have more than one replica set per Microsoft Entra tenant. Replica sets can be added to any peered virtual network in any Azure region that supports Domain Services. By adding replica sets in different Azure regions, you can provide geographical disaster recovery for legacy applications if an Azure region goes offline. For more information, see Replica sets concepts and features for managed domains.
Take a look at this video about how Domain Services integrates with your applications and workloads to provide identity services in the cloud:
To see Domain Services deployment scenarios in action, you can explore the following examples:
Domain Services features and benefits
To provide identity services to applications and VMs in the cloud, Domain Services is fully compatible with a traditional AD DS environment for operations such as domain-join, secure LDAP (LDAPS), Group Policy, DNS management, and LDAP bind and read support. LDAP write support is available for objects created in the managed domain, but not resources synchronized from Microsoft Entra ID.
To learn more about your identity options, compare Domain Services with Microsoft Entra ID, AD DS on Azure VMs, and AD DS on-premises.
The following features of Domain Services simplify deployment and management operations:
- Simplified deployment experience: Domain Services is enabled for your Microsoft Entra tenant using a single wizard in the Microsoft Entra admin center.
- Integrated with Microsoft Entra ID: User accounts, group memberships, and credentials are automatically available from your Microsoft Entra tenant. New users, groups, or changes to attributes from your Microsoft Entra tenant or your on-premises AD DS environment are automatically synchronized to Domain Services.
- Accounts in external directories linked to your Microsoft Entra ID aren't available in Domain Services. Credentials aren't available for those external directories, so can't be synchronized into a managed domain.
- Use your corporate credentials/passwords: Passwords for users in Domain Services are the same as in your Microsoft Entra tenant. Users can use their corporate credentials to domain-join machines, sign in interactively or over remote desktop, and authenticate against the managed domain.
- NTLM and Kerberos authentication: With support for NTLM and Kerberos authentication, you can deploy applications that rely on Windows-integrated authentication.
- High availability: Domain Services includes multiple domain controllers, which provide high availability for your managed domain. This high availability guarantees service uptime and resilience to failures.
- In regions that support Azure Availability Zones, these domain controllers are also distributed across zones for additional resiliency.
- Replica sets can also be used to provide geographical disaster recovery for legacy applications if an Azure region goes offline.
Some key aspects of a managed domain include the following:
- The managed domain is a stand-alone domain. It isn't an extension of an on-premises domain.
- If needed, you can create one-way outbound forest trusts from Domain Services to an on-premises AD DS environment. For more information, see Forest concepts and features for Domain Services.
- Your IT team doesn't need to manage, patch, or monitor domain controllers for this managed domain.
For hybrid environments that run AD DS on-premises, you don't need to manage AD replication to the managed domain. User accounts, group memberships, and credentials from your on-premises directory are synchronized to Microsoft Entra ID via Microsoft Entra Connect. These user accounts, group memberships, and credentials are automatically available within the managed domain.
Next steps
To learn more about Domain Services compares with other identity solutions and how synchronization works, see the following articles:
- Compare Domain Services with Microsoft Entra ID, Active Directory Domain Services on Azure VMs, and Active Directory Domain Services on-premises
- Learn how Microsoft Entra Domain Services synchronizes with your Microsoft Entra directory
- To learn how to administrator a managed domain, see management concepts for user accounts, passwords, and administration in Domain Services.
To get started, create a managed domain using the Microsoft Entra admin center.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for