Enable security and DNS audits for Microsoft Entra Domain Services
Microsoft Entra Domain Services security and DNS audits let Azure stream events to targeted resources. These resources include Azure Storage, Azure Log Analytics workspaces, or Azure Event Hub. After you enable security audit events, Domain Services sends all the audited events for the selected category to the targeted resource.
You can archive events into Azure storage and stream events into security information and event management (SIEM) software (or equivalent) using Azure Event Hubs, or do your own analysis and using Azure Log Analytics workspaces from the Microsoft Entra admin center.
Security audit destinations
You can use Azure Storage, Azure Event Hubs, or Azure Log Analytics workspaces as a target resource for Domain Services security audits. These destinations can be combined. For example, you could use Azure Storage for archiving security audit events, but an Azure Log Analytics workspace to analyze and report on the information in the short term.
The following table outlines scenarios for each destination resource type.
Important
You need to create the target resource before you enable Domain Services security audits. You can create these resources using the Microsoft Entra admin center, Azure PowerShell, or the Azure CLI.
| Target Resource | Scenario |
|---|---|
| Azure Storage | This target should be used when your primary need is to store security audit events for archival purposes. Other targets can be used for archival purposes, however those targets provide capabilities beyond the primary need of archiving. Before you enable Domain Services security audit events, first Create an Azure Storage account. |
| Azure Event Hubs | This target should be used when your primary need is to share security audit events with additional software such as data analysis software or security information & event management (SIEM) software. Before you enable Domain Services security audit events, Create an event hub using Microsoft Entra admin center |
| Azure Log Analytics Workspace | This target should be used when your primary need is to analyze and review secure audits from the Microsoft Entra admin center directly. Before you enable Domain Services security audit events, Create a Log Analytics workspace in the Microsoft Entra admin center. |
Enable security audit events using the Microsoft Entra admin center
To enable Domain Services security audit events using the Microsoft Entra admin center, complete the following steps.
Important
Domain Services security audits aren't retroactive. You can't retrieve or replay events from the past. Domain Services can only send events that occur after security audits are enabled.
Sign in to the Microsoft Entra admin center as a Global Administrator.
Search for and select Microsoft Entra Domain Services. Choose your managed domain, such as aaddscontoso.com.
In the Domain Services window, select Diagnostic settings on the left-hand side.
No diagnostics are configured by default. To get started, select Add diagnostic setting.
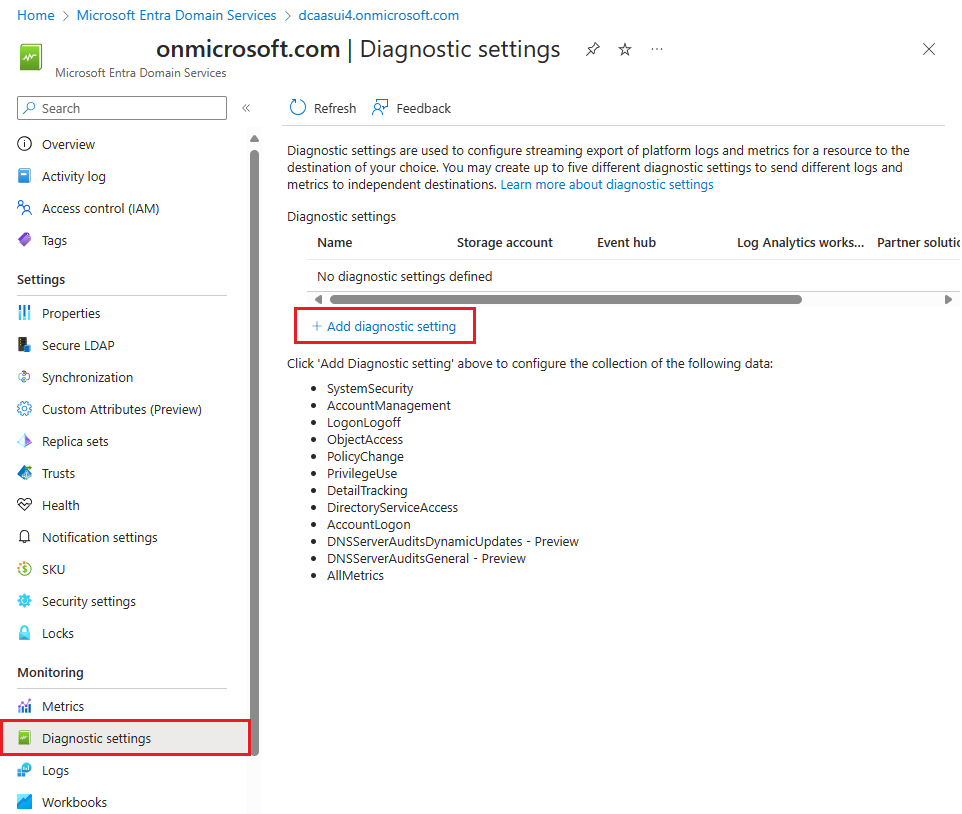
Enter a name for the diagnostic configuration, such as aadds-auditing.
Check the box for the security or DNS audit destination you want. You can choose from a Log Analytics workspace, an Azure Storage account, an Azure event hub, or a partner solution. These destination resources must already exist in your Azure subscription. You can't create the destination resources in this wizard.
- Azure Log Analytic workspaces
- Select Send to Log Analytics, then choose the Subscription and Log Analytics Workspace you want to use to store audit events.
- Azure storage
- Select Archive to a storage account, then choose Configure.
- Select the Subscription and the Storage account you want to use to archive audit events.
- When ready, choose OK.
- Azure event hubs
- Select Stream to an event hub, then choose Configure.
- Select the Subscription and the Event hub namespace. If needed, also choose an Event hub name and then Event hub policy name.
- When ready, choose OK.
- Partner solution
- Select Send to partner solution, then choose the Subscription and Destination you want to use to store audit events.
- Azure Log Analytic workspaces
Select the log categories you want included for the particular target resource. If you send the audit events to an Azure Storage account, you can also configure a retention policy that defines the number of days to retain data. A default setting of 0 retains all data and doesn't rotate events after a period of time.
You can select different log categories for each targeted resource within a single configuration. This ability lets you choose which logs categories you want to keep for Log Analytics and which logs categories you want to archive, for example.
When done, select Save to commit your changes. The target resources start to receive Domain Services audit events soon after the configuration is saved.
Enable security and DNS audit events using Azure PowerShell
To enable Domain Services security and DNS audit events using Azure PowerShell, complete the following steps. If needed, first install the Azure PowerShell module and connect to your Azure subscription.
Important
Domain Services audits aren't retroactive. You can't retrieve or replay events from the past. Domain Services can only send events that occur after audits are enabled.
Authenticate to your Azure subscription using the Connect-AzAccount cmdlet. When prompted, enter your account credentials.
Connect-AzAccountCreate the target resource for the audit events.
Azure Log Analytic workspaces - Create a Log Analytics workspace with Azure PowerShell.
Azure storage - Create a storage account using Azure PowerShell
Azure event hubs - Create an event hub using Azure PowerShell. You may also need to use the New-AzEventHubAuthorizationRule cmdlet to create an authorization rule that grants Domain Services permissions to the event hub namespace. The authorization rule must include the Manage, Listen, and Send rights.
Important
Ensure you set the authorization rule on the event hub namespace and not the event hub itself.
Get the resource ID for your Domain Services managed domain using the Get-AzResource cmdlet. Create a variable named $aadds.ResourceId to hold the value:
$aadds = Get-AzResource -name aaddsDomainNameConfigure the Azure Diagnostic settings using the Set-AzDiagnosticSetting cmdlet to use the target resource for Microsoft Entra Domain Services audit events. In the following examples, the variable $aadds.ResourceId is used from the previous step.
Azure storage - Replace storageAccountId with your storage account name:
Set-AzDiagnosticSetting ` -ResourceId $aadds.ResourceId ` -StorageAccountId storageAccountId ` -Enabled $trueAzure event hubs - Replace eventHubName with the name of your event hub and eventHubRuleId with your authorization rule ID:
Set-AzDiagnosticSetting -ResourceId $aadds.ResourceId ` -EventHubName eventHubName ` -EventHubAuthorizationRuleId eventHubRuleId ` -Enabled $trueAzure Log Analytic workspaces - Replace workspaceId with the ID of the Log Analytics workspace:
Set-AzureRmDiagnosticSetting -ResourceId $aadds.ResourceId ` -WorkspaceID workspaceId ` -Enabled $true
Query and view security and DNS audit events using Azure Monitor
Log Analytic workspaces let you view and analyze the security and DNS audit events using Azure Monitor and the Kusto query language. This query language is designed for read-only use that boasts power analytic capabilities with an easy-to-read syntax. For more information to get started with Kusto query languages, see the following articles:
- Azure Monitor documentation
- Get started with Log Analytics in Azure Monitor
- Get started with log queries in Azure Monitor
- Create and share dashboards of Log Analytics data
The following sample queries can be used to start analyzing audit events from Domain Services.
Sample query 1
View all the account lockout events for the last seven days:
AADDomainServicesAccountManagement
| where TimeGenerated >= ago(7d)
| where OperationName has "4740"
Sample query 2
View all the account lockout events (4740) between June 3, 2020 at 9 a.m. and June 10, 2020 midnight, sorted ascending by the date and time:
AADDomainServicesAccountManagement
| where TimeGenerated >= datetime(2020-06-03 09:00) and TimeGenerated <= datetime(2020-06-10)
| where OperationName has "4740"
| sort by TimeGenerated asc
Sample query 3
View account sign-in events seven days ago (from now) for the account named user:
AADDomainServicesAccountLogon
| where TimeGenerated >= ago(7d)
| where "user" == tolower(extract("Logon Account:\t(.+[0-9A-Za-z])",1,tostring(ResultDescription)))
Sample query 4
View account sign-in events seven days ago from now for the account named user that attempted to sign in using a bad password (0xC0000006a):
AADDomainServicesAccountLogon
| where TimeGenerated >= ago(7d)
| where "user" == tolower(extract("Logon Account:\t(.+[0-9A-Za-z])",1,tostring(ResultDescription)))
| where "0xc000006a" == tolower(extract("Error Code:\t(.+[0-9A-Fa-f])",1,tostring(ResultDescription)))
Sample query 5
View account sign-in events seven days ago from now for the account named user that attempted to sign in while the account was locked out (0xC0000234):
AADDomainServicesAccountLogon
| where TimeGenerated >= ago(7d)
| where "user" == tolower(extract("Logon Account:\t(.+[0-9A-Za-z])",1,tostring(ResultDescription)))
| where "0xc0000234" == tolower(extract("Error Code:\t(.+[0-9A-Fa-f])",1,tostring(ResultDescription)))
Sample query 6
View the number of account sign-in events seven days ago from now for all sign-in attempts that occurred for all locked out users:
AADDomainServicesAccountLogon
| where TimeGenerated >= ago(7d)
| where "0xc0000234" == tolower(extract("Error Code:\t(.+[0-9A-Fa-f])",1,tostring(ResultDescription)))
| summarize count()
Audit security and DNS event categories
Domain Services security and DNS audits align with traditional auditing for traditional AD DS domain controllers. In hybrid environments, you can reuse existing audit patterns so the same logic may be used when analyzing the events. Depending on the scenario you need to troubleshoot or analyze, the different audit event categories need to be targeted.
The following audit event categories are available:
| Audit Category Name | Description |
|---|---|
| Account Logon | Audits attempts to authenticate account data on a domain controller or on a local Security Accounts Manager (SAM). -Logon and Logoff policy settings and events track attempts to access a particular computer. Settings and events in this category focus on the account database that is used. This category includes the following subcategories: -Audit Credential Validation -Audit Kerberos Authentication Service -Audit Kerberos Service Ticket Operations -Audit Other Logon/Logoff Events |
| Account Management | Audits changes to user and computer accounts and groups. This category includes the following subcategories: -Audit Application Group Management -Audit Computer Account Management -Audit Distribution Group Management -Audit Other Account Management -Audit Security Group Management -Audit User Account Management |
| DNS Server | Audits changes to DNS environments. This category includes the following subcategories: - DNSServerAuditsDynamicUpdates (preview) - DNSServerAuditsGeneral (preview) |
| Detail Tracking | Audits activities of individual applications and users on that computer, and to understand how a computer is being used. This category includes the following subcategories: -Audit DPAPI Activity -Audit PNP activity -Audit Process Creation -Audit Process Termination -Audit RPC Events |
| Directory Services Access | Audits attempts to access and modify objects in Active Directory Domain Services (AD DS). These audit events are logged only on domain controllers. This category includes the following subcategories: -Audit Detailed Directory Service Replication -Audit Directory Service Access -Audit Directory Service Changes -Audit Directory Service Replication |
| Logon-Logoff | Audits attempts to log on to a computer interactively or over a network. These events are useful for tracking user activity and identifying potential attacks on network resources. This category includes the following subcategories: -Audit Account Lockout -Audit User/Device Claims -Audit IPsec Extended Mode -Audit Group Membership -Audit IPsec Main Mode -Audit IPsec Quick Mode -Audit Logoff -Audit Logon -Audit Network Policy Server -Audit Other Logon/Logoff Events -Audit Special Logon |
| Object Access | Audits attempts to access specific objects or types of objects on a network or computer. This category includes the following subcategories: -Audit Application Generated -Audit Certification Services -Audit Detailed File Share -Audit File Share -Audit File System -Audit Filtering Platform Connection -Audit Filtering Platform Packet Drop -Audit Handle Manipulation -Audit Kernel Object -Audit Other Object Access Events -Audit Registry -Audit Removable Storage -Audit SAM -Audit Central Access Policy Staging |
| Policy Change | Audits changes to important security policies on a local system or network. Policies are typically established by administrators to help secure network resources. Monitoring changes or attempts to change these policies can be an important aspect of security management for a network. This category includes the following subcategories: -Audit Audit Policy Change -Audit Authentication Policy Change -Audit Authorization Policy Change -Audit Filtering Platform Policy Change -Audit MPSSVC Rule-Level Policy Change -Audit Other Policy Change |
| Privilege Use | Audits the use of certain permissions on one or more systems. This category includes the following subcategories: -Audit Non-Sensitive Privilege Use -Audit Sensitive Privilege Use -Audit Other Privilege Use Events |
| System | Audits system-level changes to a computer not included in other categories and that have potential security implications. This category includes the following subcategories: -Audit IPsec Driver -Audit Other System Events -Audit Security State Change -Audit Security System Extension -Audit System Integrity |
Event IDs per category
Domain Services security and DNS audits record the following event IDs when the specific action triggers an auditable event:
| Event Category Name | Event IDs |
|---|---|
| Account Logon security | 4767, 4774, 4775, 4776, 4777 |
| Account Management security | 4720, 4722, 4723, 4724, 4725, 4726, 4727, 4728, 4729, 4730, 4731, 4732, 4733, 4734, 4735, 4737, 4738, 4740, 4741, 4742, 4743, 4754, 4755, 4756, 4757, 4758, 4764, 4765, 4766, 4780, 4781, 4782, 4793, 4798, 4799, 5376, 5377 |
| Detail Tracking security | None |
| DNS Server | 513-523, 525-531, 533-537, 540-582 |
| DS Access security | 5136, 5137, 5138, 5139, 5141 |
| Logon-Logoff security | 4624, 4625, 4634, 4647, 4648, 4672, 4675, 4964 |
| Object Access security | None |
| Policy Change security | 4670, 4703, 4704, 4705, 4706, 4707, 4713, 4715, 4716, 4717, 4718, 4719, 4739, 4864, 4865, 4866, 4867, 4904, 4906, 4911, 4912 |
| Privilege Use security | 4985 |
| System security | 4612, 4621 |
Next steps
For specific information on Kusto, see the following articles:
- Overview of the Kusto query language.
- Kusto tutorial to familiarize you with query basics.
- Sample queries that help you learn new ways to see your data.
- Kusto best practices to optimize your queries for success.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for