What's new in Microsoft Defender for Cloud Apps
Applies to: Microsoft Defender for Cloud Apps
This article is updated frequently to let you know what's new in the latest release of Microsoft Defender for Cloud Apps.
For more information on what's new with other Microsoft Defender security products, see:
- What's new in Microsoft Defender XDR
- What's new in Microsoft Defender for Endpoint
- What's new in Microsoft Defender for Identity
For news about earlier releases, see Archive of past updates for Microsoft Defender for Cloud Apps.
The classic Microsoft Defender for Cloud Apps portal experience and functionality have been converged into the Microsoft Defender XDR Portal. As of June 2024, all customers using the classic Defender for Cloud Apps portal are automatically redirected to Microsoft Defender XDR, with no option to revert back to the classic portal.
For more information, see Microsoft Defender for Cloud Apps in Microsoft Defender XDR.
Now, when you're creating access or session policies with Conditional Access app control, your Microsoft Entra ID apps are automatically onboarded and available for you to use in your policies.
When creating your access and session policies, select your apps by filtering for Automated Azure AD onboarding, for Microsoft Entra ID apps, or Manual onboarding, for non-Microsoft IdP apps.
For example:
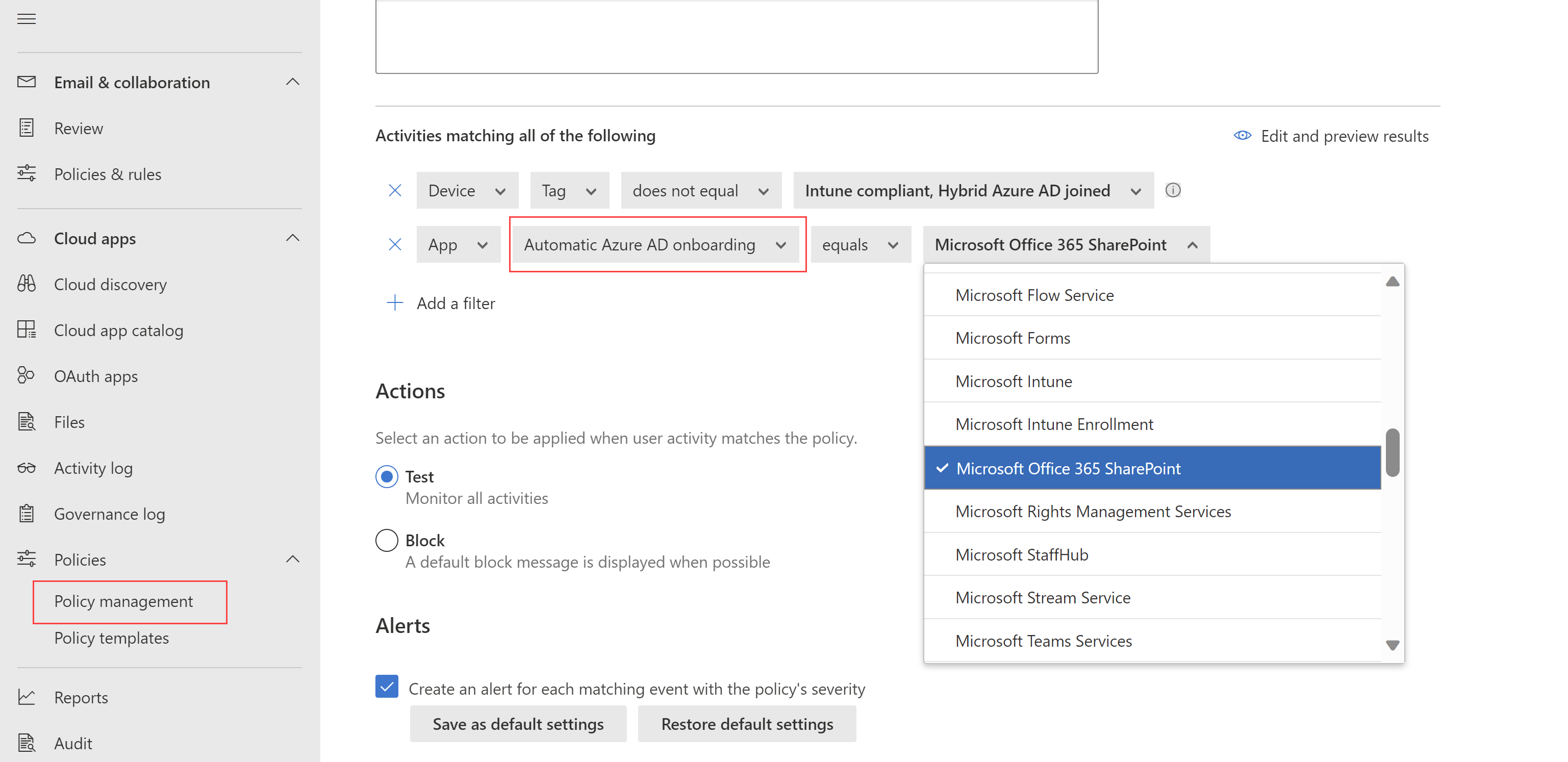
Extra steps for using Conditional Access app control still include:
- Creating a Microsoft Entra ID Conditional Access policy for the apps you want to control with Defender for Cloud Apps Conditional Access app control.
- Manual steps to onboard non-Microsoft IdP apps, including configuring your IdP to work with Defender for Cloud Apps.
For more information, see:
- Protect apps with Microsoft Defender for Cloud Apps Conditional Access app control
- Conditional Access app control process flow
- Create access policies
- Create session policies
Defender for Cloud Apps now supports cloud app discovery on macOS devices together with the Microsoft Defender for Endpoint integration. Defender for Cloud Apps and Defender for Endpoint together provide a seamless Shadow IT visibility and control solution.
Together with this enhancement, the Win10 Endpoint Users option on the Cloud Discovery page has been renamed to Defender-managed endpoints.
For more information, see:
- Integrate Microsoft Defender for Endpoint with Microsoft Defender for Cloud Apps
- Investigate apps discovered by Microsoft Defender for Endpoint
Microsoft Defender for Cloud Apps log collector now supports Azure Kubernetes Service (AKS) when the receiver type is Syslog-tls, and you can configure automatic log collection on AKS for continuous reporting with Defender for Cloud Apps.
For more information, see Configure automatic log upload using Docker on Azure Kubernetes Service (AKS).
Defender for Cloud Apps users who use advanced hunting in the Microsoft Defender portal can now use the new AuditSource and SessionData columns for queries and detection rules. Using this data allows for queries that consider specific audit sources, including access and session control, and queries by specific inline sessions.
For more information, see Advanced Hunting "CloudAppEvents" Data schema.
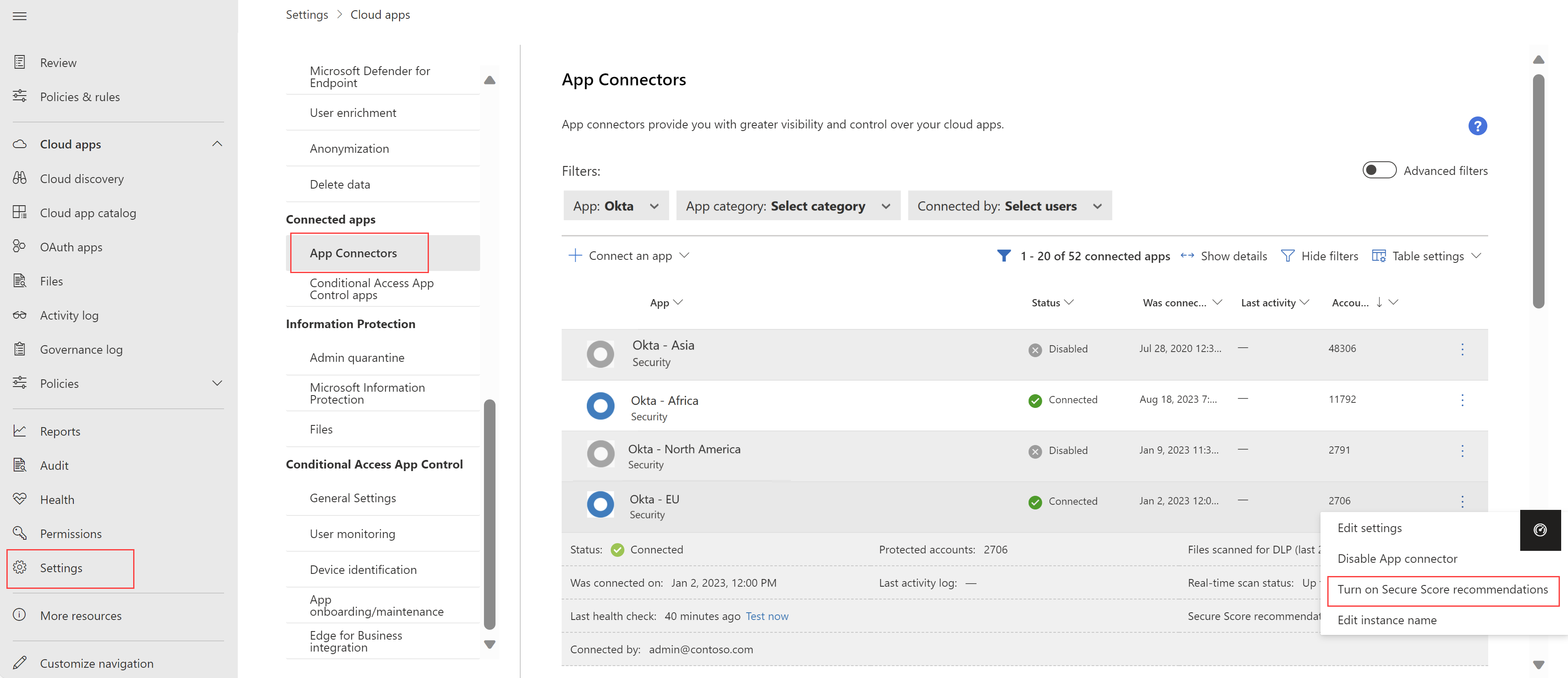
Defender for Cloud Apps now supports SaaS security posture management (SSPM) across multiple instances of the same app. For example, if you have multiple instances of Okta, you can configure Secure Score recommendations for each instance individually. Each instance shows up as a separate item on the App Connectors page. For example:
For more information, see SaaS security posture management (SSPM).
Defender for Cloud Apps in the Microsoft Defender portal - General Availability and advance notice for redirection
The Defender for Cloud Apps experience in the Microsoft Defender portal is generally available, and the automatic redirection from the classic portal is on by default for all customers.
Starting June 16, 2024, the redirection toggle will no longer be available. From then on, all users accessing the classic Microsoft Defender for Cloud Apps portal will be automatically rerouted to the Microsoft Defender portal, with no option to opt out.
To prepare for this change, we recommend that any customers still using the classic portal move operations to the Microsoft Defender portal. For more information, see Microsoft Defender for Cloud Apps in Microsoft Defender XDR.
Now, preview customers can manage settings for preview features together with other Microsoft Defender XDR preview features.
Select Settings > Microsoft Defender XDR > General > Preview to toggle preview features on or off as needed. For example:
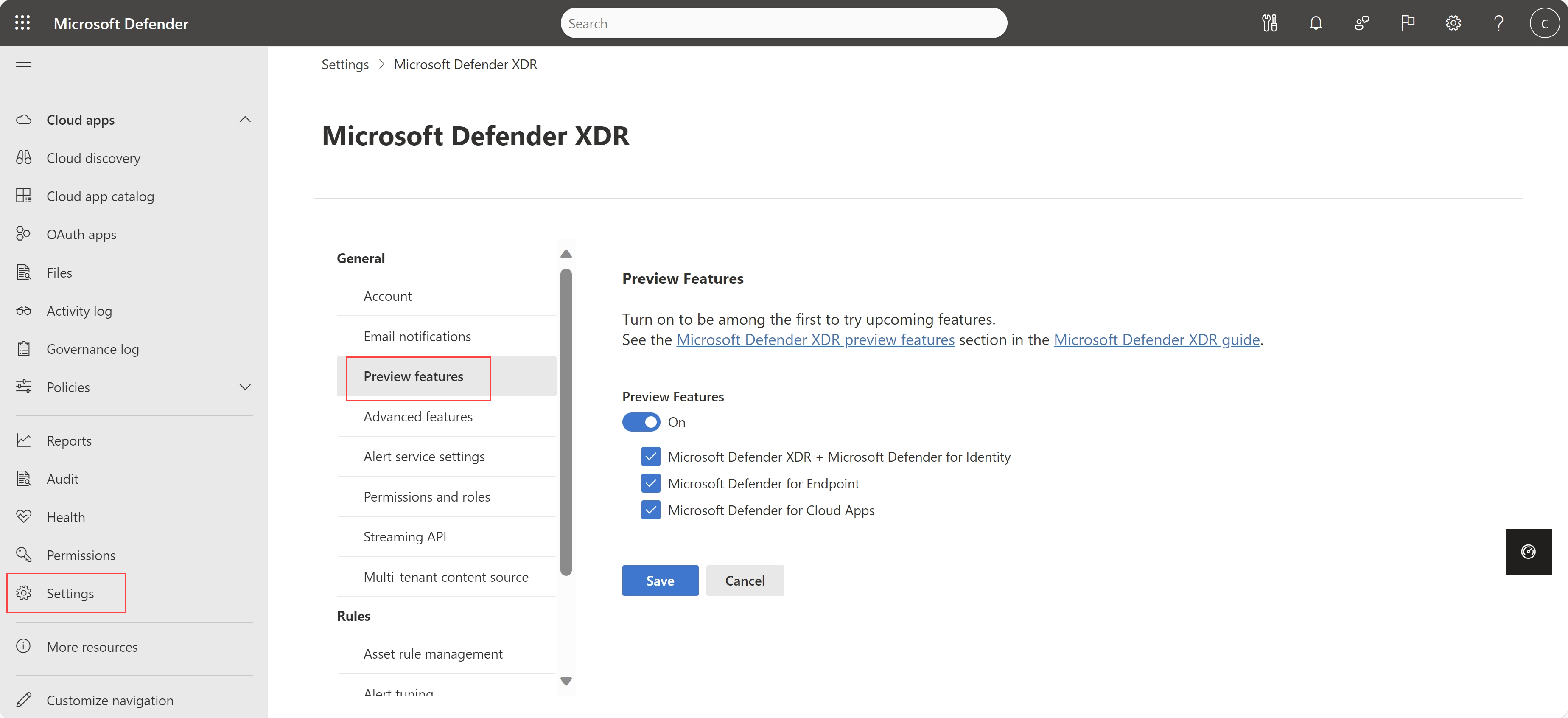
Customers not yet using preview features continue to see the legacy settings under Settings > Cloud apps > System > Preview features.
For more information, see Microsoft Defender XDR preview features.
App governance features in Defender for Cloud Apps are now available in government clouds. For more information, see:
- App governance in Microsoft Defender for Cloud Apps
- Microsoft Defender for Cloud Apps for US Government offerings
Now you can complete the process for encrypting Defender for Cloud Apps data at rest with your own key by enabling data encryption from the Settings area of the Microsoft Defender portal.
This feature is now limited on the classic Microsoft Defender for Cloud Apps portal, and is available only from the Microsoft Defender portal.
For more information, see Encrypt Defender for Cloud Apps data at rest with your own key (BYOK).
We released a new version of a log collector with the latest vulnerability fixes. The new version is columbus-0.272.0-signed.jar, and the image name is mcaspublic.azurecr.io/public/mcas/logcollector, with the tag latest/0.272.0.
Changes include upgrading dependencies, such as:
- amazon-corretto
- ubuntu
- libssl
- oauthlib
- logback
- setuptools
For more information, see Advanced log collector management.
Microsoft Defender for Cloud Apps log collector now supports Podman, and you can configure automatic log collection on Podman for continuous reporting with Defender for Cloud Apps.
Automatic log collection is supported using a Docker container on multiple operating systems. For Linux distributions using RHEL version 7.1 and higher, you must use Podman as the container's runtime system.
For more information, see Configure automatic log upload using Podman.
Defender for Cloud Apps users who use advanced hunting in the Microsoft Defender portal can now use the new LastSeenForUser and UncommonForUser columns for queries and detections rules. Using this data helps to rule out false positives and find anomalies.
For more information, see Advanced Hunting "CloudAppEvents" Data schema.
Defender for Cloud Apps now provides new detections for risky user activities in Microsoft Copilot for Microsoft 365 with the Microsoft 365 connector.
- Related alerts are shown together with other Microsoft Defender XDR alerts, in the Microsoft Defender portal.
- Copilot for Microsoft 365 activities is available in the Defender for Cloud Apps activity log.
- In the Microsoft Defender portal's Advanced hunting page, Copilot for Microsoft 365 activities are available in the CloudAppEvents table, under the Microsoft Copilot for Microsoft 365 application.
For more information, see:
- Get started with Microsoft Copilot for Microsoft 365
- How Defender for Cloud Apps helps protect your Microsoft 365 environment
- Investigate alerts in Microsoft Defender XDR
- Defender for Cloud Apps Activity log
- Proactively hunt for threats with advanced hunting
- CloudAppEvents table in the advanced hunting schema
Defender for Cloud Apps users who use Microsoft Edge for Business and are subject to session policies are now protected directly from within the browser. In-browser protection reduces the need for proxies, improving both security and productivity.
Protected users experience a smooth experience with their cloud apps, without latency or app compatibility issues, and with a higher level of security protection.
In-browser protection is turned on by default, and is being gradually rolled out across tenants, starting early in March 2024.
For more information, see In-browser protection with Microsoft Edge for Business (Preview), Protect apps with Microsoft Defender for Cloud Apps Conditional Access App Control, and Session policies.
Defender for Cloud Apps in the Microsoft Defender portal now available to all Defender for Cloud Apps roles
The Defender for Cloud Apps experience in the Microsoft Defender portal is now available for all Defender for Cloud Apps roles, including the following roles that were previously limited:
- App/Instance admin
- User group admin
- Cloud Discovery global admin
- Cloud Discovery report admin
For more information, see Built-in admin roles in Defender for Cloud Apps.
Defender for Cloud Apps provides you with security recommendations for your SaaS applications to help you prevent possible risks. These recommendations are shown via Microsoft Secure Score once you have a connector to an application.
Defender for Cloud Apps has now enhanced its SSPM support in general availability by including the following apps:
SSPM is also now supported for Google Workspace in General Availability.
Note
If you already have a connector to one of these apps, your score in Secure score might automatically update accordingly.
For more information, see:
- SaaS security posture management (SSPM)
- User, app governance, and security configuration visibility
- Microsoft Secure Score
We've added the following new alerts for App governance customers:
- Application initiating multiple failed KeyVault read activity with no success
- Dormant OAuth App predominantly using MS Graph or Exchange Web Services recently seen to be accessing Azure Resource Manager workloads
For more information, see App governance in Microsoft Defender for Cloud Apps.
Defender for Cloud Apps now supports SaaS security posture management (SSPM) across multiple instances of the same app. For example, if you have multiple instances of AWS, you can configure Secure Score recommendations for each instance individually. Each instance shows up as a separate item on the App Connectors page. For example:
For more information, see SaaS security posture management (SSPM).
Limitation removed for the number of files that can be controlled for uploading in session policies (Preview)
Session policies now support control over uploading folders with more than 100 files, with no limit to the number of files that can be included in the upload.
For more information, see Protect apps with Microsoft Defender for Cloud Apps Conditional Access App Control.
The classic Microsoft Defender for Cloud Apps portal experience and functionality have been converged into the Microsoft Defender XDR Portal. As of January 9, 2024, customers using the classic Defender for Cloud Apps portal with Preview features are automatically redirected to Microsoft Defender XDR, with no option to revert back to the classic portal.
For more information, see:
- For a description of releases prior to those listed here, see Past releases of Microsoft Cloud App Security.
If you run into any problems, we're here to help. To get assistance or support for your product issue, please open a support ticket.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for